Guidance to Assist Non-Federal Entities to Share Cyber Threat Indicators and Defensive Measures with Federal Entities under the Cybersecurity Information Sharing Act of 2015: Department of Homeland Security, Department of Justice, Penny
Guidance to Assist Non-Federal Entities to Share Cyber Threat Indicators and Defensive Measures with Federal Entities under the

Heather Enlow & Chris Ingram - Cybersecurity Act of 2015 and Other Hot Privacy and Cybersecurity Topics

Singapore's new Cybersecurity Act comes into force: Here's what you need to know | Data Protection Report

The Cybersecurity Information Sharing Act (CISA) - The Henry M. Jackson School of International Studies
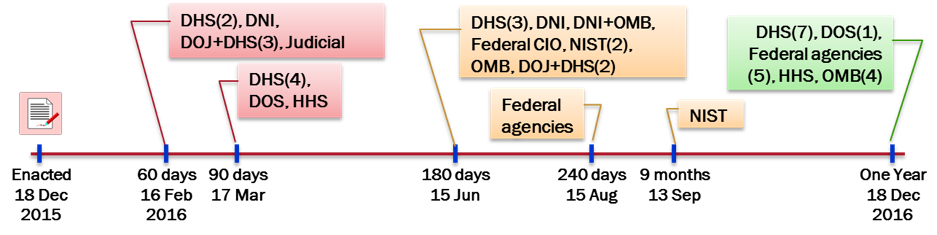
Implementing the Cybersecurity Act of 2015: A Public-Private Specifications Approach | Yaana Technologies, LLC

The Cybersecurity Information Sharing Act of 2015 (CISA): Is It the Right Answer? | Infosec Resources
Cybersecurity Act of 2015 Report: EPA's Policies and Procedures to Protect Systems With Personally Identifiable Information

The potential impact of the 2015 Cybersecurity Information Sharing Act (CISA) - The Henry M. Jackson School of International Studies
Guidance to Assist Non-Federal Entities to Share Cyber Threat Indicators and Defensive Measures with Federal Entities under the